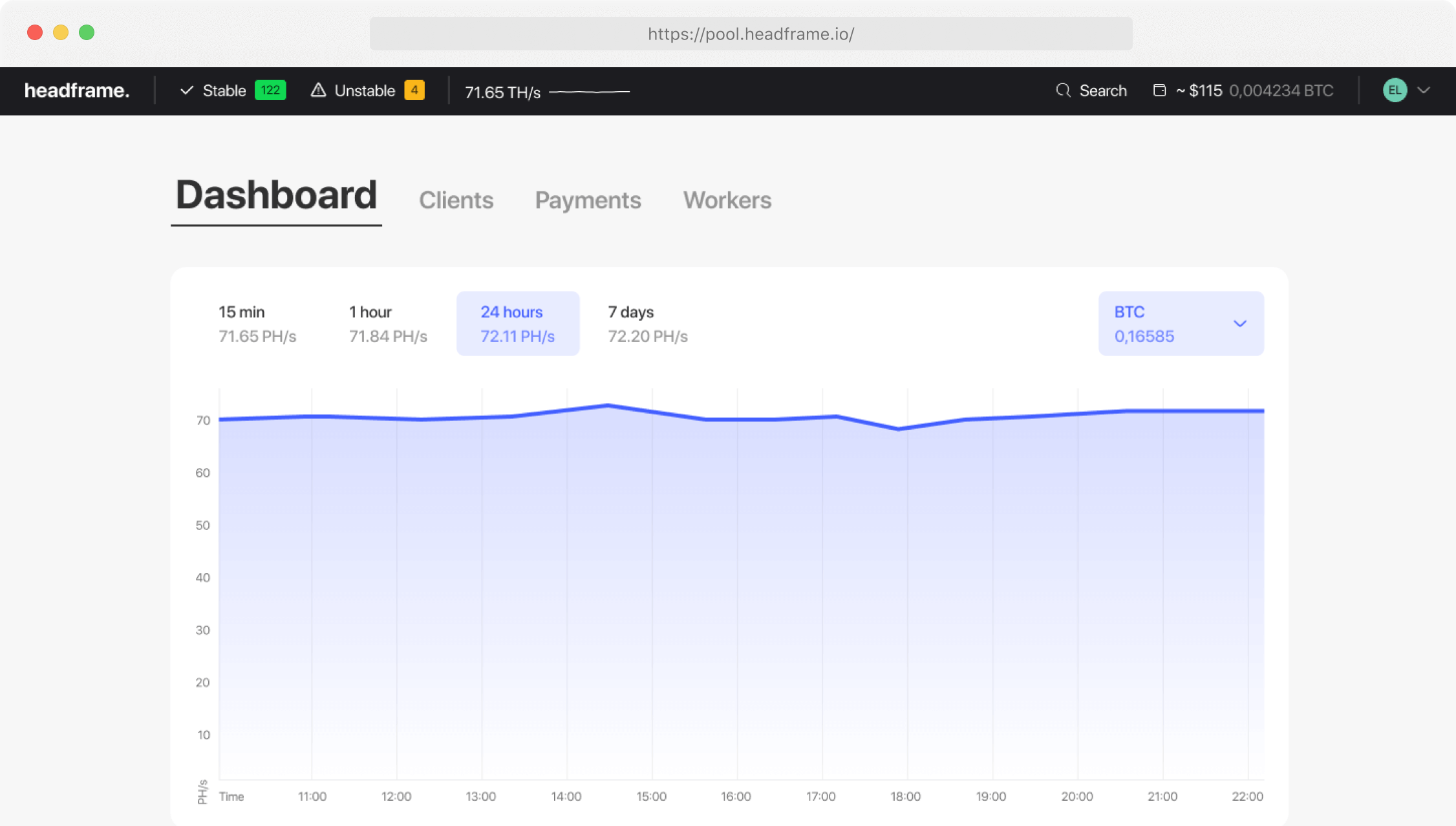
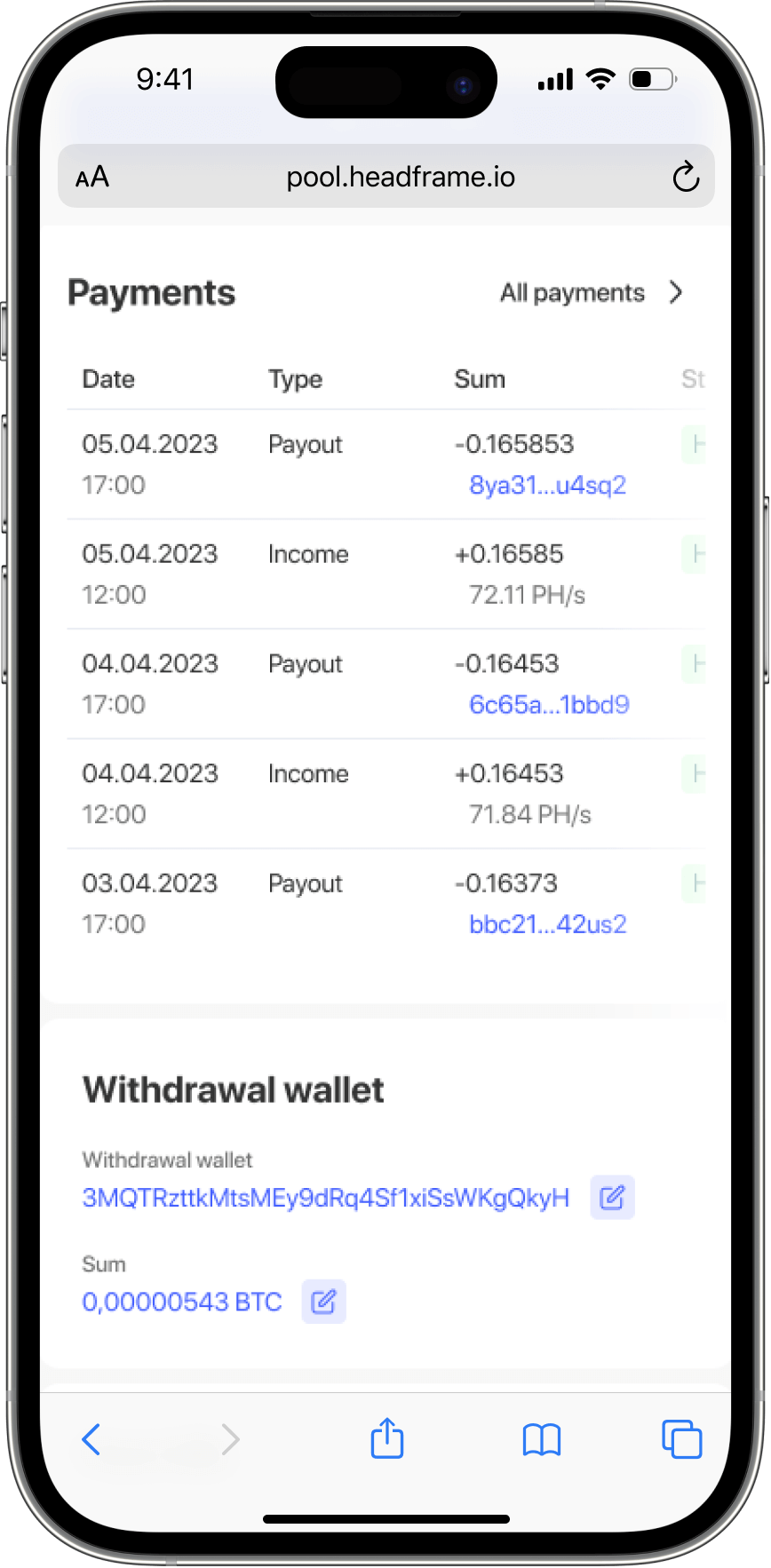
Digital Security: Protecting Assets in Mining Pools
Digital security is a critically important aspect for mining pools, as they attract the attention of hackers and malicious actors seeking access to significant assets. Ensuring reliable protection of assets in mining pools requires a comprehensive approach that includes using advanced technologies and strategies to prevent threats. In this text, we will examine the main methods of digital security that help protect assets in mining pools and discuss how to apply them effectively.
Earn more money with Headframe
Join a mining pool and get the best profitability in mining. Already more than 10,000 miners trust Headframe.
Let’s start with the importance of ensuring security at the infrastructure level. Mining pools operate on powerful servers that process enormous volumes of data. Protecting these servers from physical and virtual threats is the first step toward creating a secure system. Using modern data encryption methods helps prevent unauthorized access and protect information about transactions and accounts. Regular software and operating system updates also play a key role in eliminating vulnerabilities that hackers could exploit.
Two-factor authentication (2FA) is one of the most effective methods for protecting participants’ accounts in mining pools. 2FA requires users to provide two forms of identification before accessing their accounts, significantly complicating tasks for malicious actors. This can be a combination of a password and a one-time code sent to the user’s mobile device. Implementing two-factor authentication helps protect accounts even if the user’s password has been compromised.
Monitoring network activity and detecting anomalies are essential aspects of digital security. Modern monitoring systems use artificial intelligence and machine learning to analyze network traffic and detect suspicious activity in real time. This allows for rapid response to potential threats and prevents attacks before they cause significant damage. Regular security audits and penetration testing also help identify and address system vulnerabilities.
Protection against distributed denial-of-service (DDoS) attacks is crucial for mining pools. DDoS attacks can overload pool servers, making them unavailable to users and disrupting normal operations. Using cloud-based DDoS protection services and implementing traffic filtering technologies help protect pool infrastructure from such threats. These measures include automatic resource scaling and intelligent filters that can detect and block malicious traffic.
Data encryption is another important component of digital security. Encryption ensures the protection of data transmitted between pool participants and its servers, making it inaccessible to malicious actors. Using advanced encryption algorithms, such as AES-256, helps ensure a high level of security. It is also important to encrypt data stored on servers to prevent its leakage in case of physical access to the equipment.
Access management and user rights control are also crucial for protecting mining pool assets. It is necessary to ensure that only authorized users have access to critical systems and data. Implementing the principle of least privilege helps restrict user access to only the resources necessary for their tasks. This reduces the risk of internal threats and prevents unauthorized access to confidential information.
Data backup and disaster recovery planning are vital aspects of asset protection. Regularly creating data backups helps ensure their preservation in case of a cyberattack or technical failure. Storing backups in different geographical locations and using various backup methods, such as full and incremental backups, helps minimize data loss. Disaster recovery planning includes developing procedures and instructions for quickly restoring pool operations in case of an incident.
Training and raising awareness among employees and pool participants are integral parts of a digital security strategy. Users need to be informed about current threats and protection methods to minimize the risk of human error. Regular training sessions and security seminars help increase knowledge and readiness to respond to incidents. It is also important to develop and implement a security policy that defines the main rules and procedures for all pool participants.
Proper management of encryption keys is a crucial aspect of digital security. Encryption keys should be stored in secure locations and accessible only to authorized users. Using hardware security modules (HSM) and other secure solutions for key storage and management helps prevent their compromise. Regular key rotation and the use of multi-factor authentication for access to keys are also important security measures.
Collaboration with professional security service providers and consulting firms can significantly enhance the level of protection for the mining pool. These organizations have the experience and knowledge necessary for conducting security audits, developing protection strategies, and responding to incidents. Utilizing professional services helps identify and address system weaknesses and ensures compliance with international security standards.
Thus, protecting assets in mining pools requires a comprehensive approach that includes using advanced technologies, effective access management, data encryption, network activity monitoring, user training, and collaboration with professional security service providers. Attention to detail and a readiness for continuous improvement and adaptation help ensure a high level of digital security and protect pool participants’ assets from various threats. Creating and maintaining a reliable security system contributes to the sustainable development and success of mining pools in the face of constantly changing cyber threats.