Analysis of Mining Pool Hacking Cases and Prevention Measures
Mining pools are a crucial part of the cryptocurrency ecosystem, pooling resources from numerous miners to enhance the efficiency and stability of cryptocurrency mining. However, they also become targets for hackers and malicious actors seeking access to the funds and data of pool participants. Let’s examine cases of mining pool hacks and measures that can be taken to prevent them and ensure security.
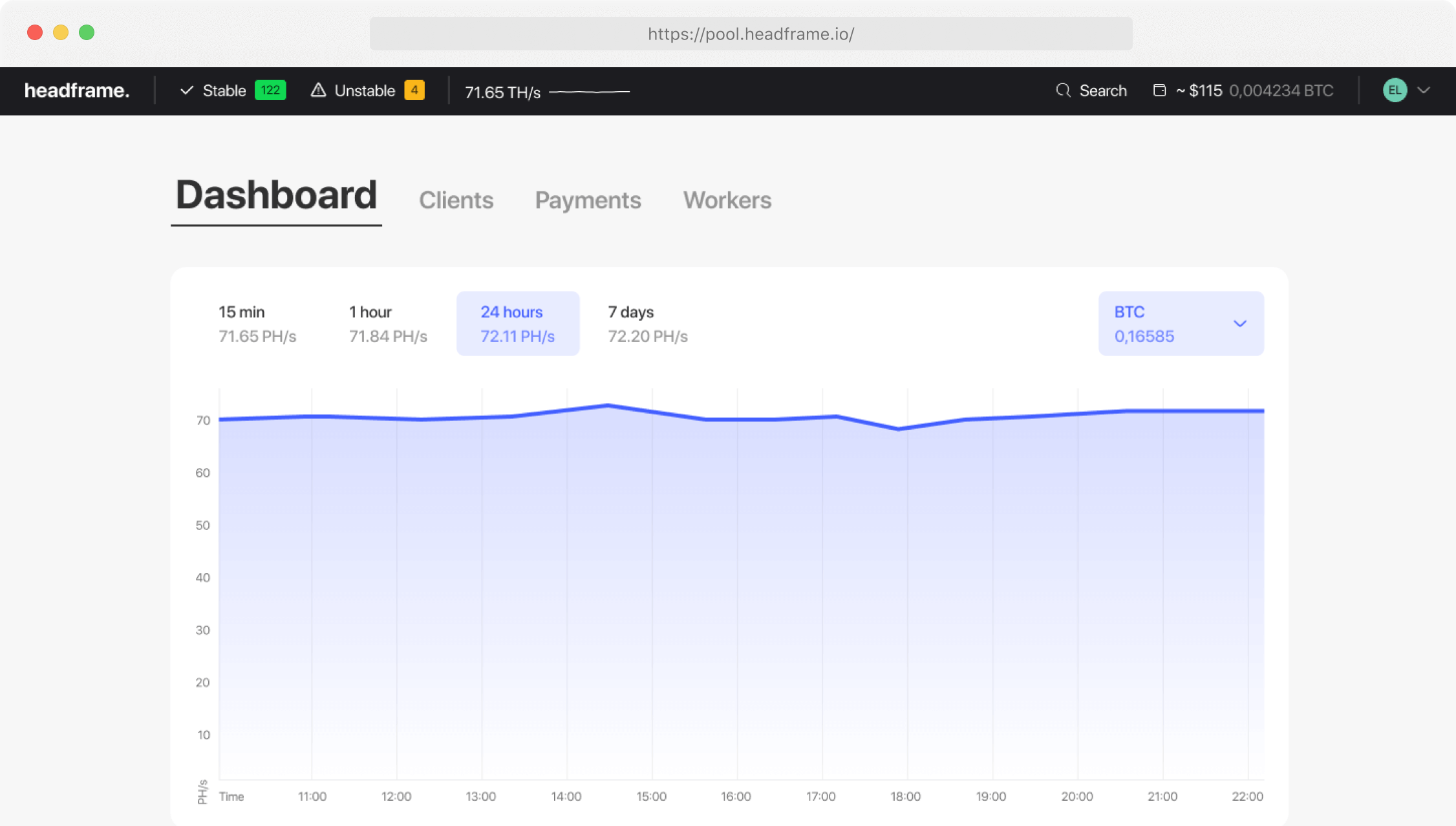
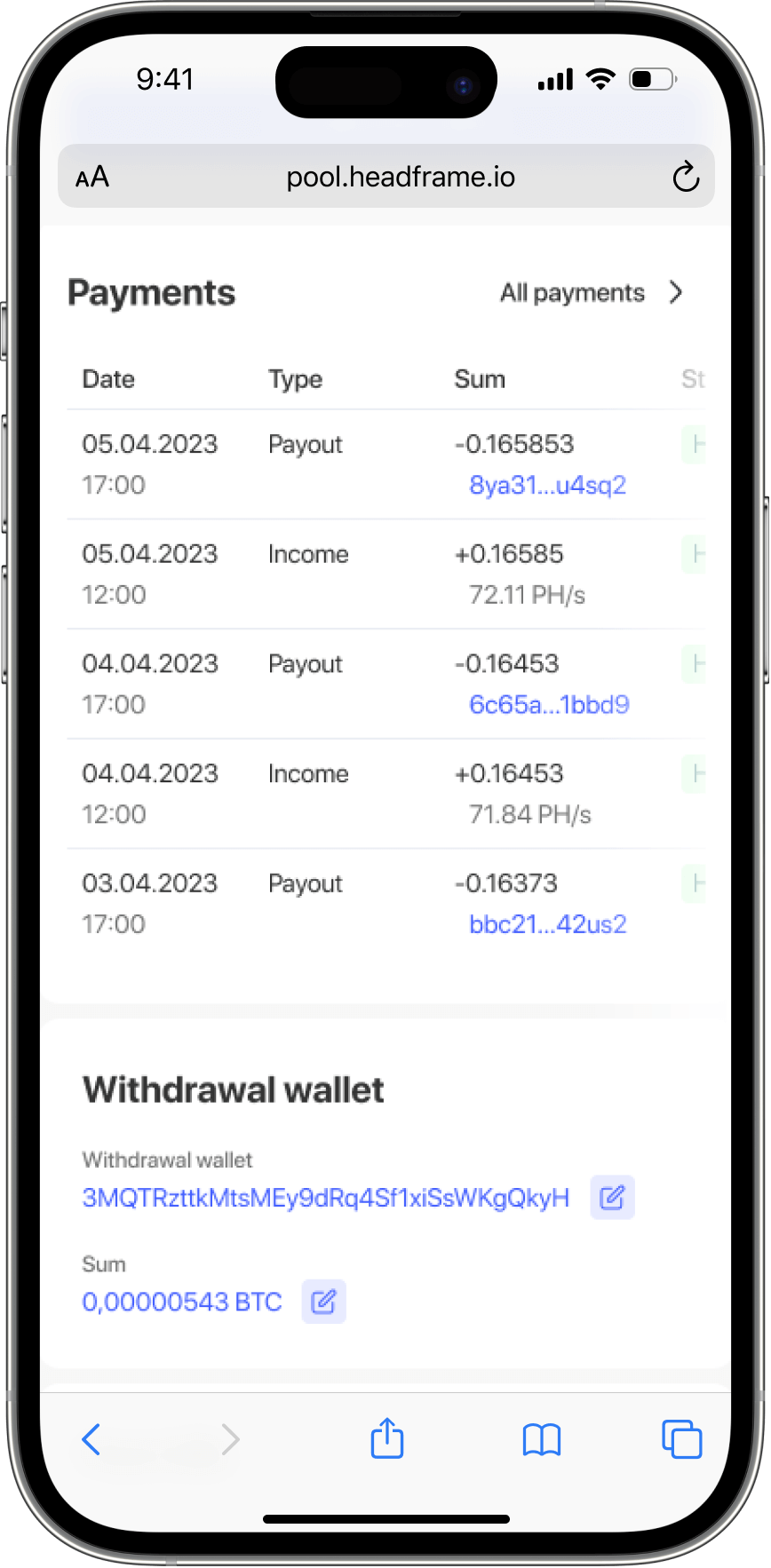
Earn more money with Headframe
Join a mining pool and get the best profitability in mining. Already more than 10,000 miners trust Headframe.
In recent years, several significant incidents of mining pool hacks have highlighted vulnerabilities in their security systems. One of the most well-known cases was the NiceHash pool hack in 2017, where hackers accessed the pool’s server and stole bitcoins worth approximately $64 million. This incident underscored the importance of robust server and data protection and the necessity for regular updates and enhancements to security systems.
Another notable case involved the Verge mining pool in 2018. Hackers exploited a vulnerability in the Verge blockchain code to conduct an attack that allowed them to mine a large number of coins in a short period. This incident demonstrated the importance of thorough blockchain code testing and swift responses to identified vulnerabilities.
Hacks of mining pools can have severe consequences not only for the pools themselves but also for all their participants. The loss of funds and data can lead to significant financial losses and undermine trust in the pool. Additionally, such incidents can negatively impact the reputation of the entire cryptocurrency industry, raising doubts about the reliability and security of mining operations.
To prevent hacks and ensure security, mining pools must adopt comprehensive measures to protect their systems and data. One key measure is the use of modern data encryption methods to safeguard information from unauthorized access. Encrypting data both at rest and in transit helps secure it and prevent theft.
Additionally, it is crucial to implement multi-factor authentication (MFA) for access to pool management systems. MFA requires users to verify their identity using multiple factors such as passwords, SMS codes, or biometric data. This significantly complicates the task for hackers and helps prevent unauthorized access to pool systems.
Regular security audits and penetration testing are also important measures to ensure the security of mining pools. Security audits help identify and address system vulnerabilities, while penetration testing assesses the effectiveness of security measures. Conducting such checks with the involvement of independent experts helps enhance the level of security and confidence in data protection.
Updating software and security systems is another crucial measure to prevent hacks. Developers constantly release updates and patches to fix identified vulnerabilities and improve protection. Mining pools must promptly install these updates and ensure that all systems run the latest software versions.
Education and training of pool participants also play an important role in ensuring security. Training miners and pool operators in data protection methods and safe system usage practices helps reduce the risk of hacks. Conducting regular security training sessions and seminars helps raise participant awareness and improve their data protection skills.
Furthermore, it is important to establish incident response procedures that allow for rapid response to identified threats and minimize their impact. This may include creating incident response teams, developing action plans, and conducting training exercises. Quick and effective incident response helps mitigate damage and prevent further attacks.
Collaboration with other mining pools and organizations also helps improve security. Sharing information about new threats and vulnerabilities, conducting joint research, and developing security standards enhance protection for all industry participants. Joint efforts to ensure security contribute to creating a more resilient and protected cryptocurrency ecosystem.
Regulatory aspects also play a significant role in ensuring the security of mining pools. Compliance with laws and regulations, such as the General Data Protection Regulation (GDPR) in the European Union, helps ensure the legitimacy and transparency of operations. Regulators may also require security audits and reporting on implemented protection measures. Adhering to regulatory requirements strengthens the trust of participants and investors in mining pools and promotes their long-term success.
In conclusion, the analysis of mining pool hacks and preventive measures shows that security is a critically important aspect for the successful operation of mining pools. Using modern data encryption methods, multi-factor authentication, regular security audits and penetration testing, software updates, participant training, incident response procedures, collaboration with other pools, and compliance with regulatory requirements are all key measures in ensuring the protection of mining pool data and systems. Understanding and implementing these measures help mining pools effectively counter threats and ensure long-term stability and security in the cryptocurrency industry.