Security tips for using mining pools safely
Cryptocurrency mining has evolved into a highly competitive and sophisticated industry. For many miners, joining a mining pool is a strategic move to maximize efficiency and earnings. However, the collaborative nature of mining pools introduces specific security risks that miners must address to protect their investments. This guide provides essential security tips for safely using mining pools, ensuring that your cryptocurrency mining efforts remain secure and profitable.
Earn more money with Headframe
Join a mining pool and get the best profitability in mining. Already more than 10,000 miners trust Headframe.
One of the primary security concerns when using a mining pool is the potential for hacking and unauthorized access. Cybercriminals are constantly devising new methods to exploit vulnerabilities in mining operations. To mitigate these risks, it is crucial to choose a reputable mining pool with robust security measures in place. Reputable pools often have a proven track record and positive reviews from the mining community, indicating their reliability and commitment to security.
When selecting a mining pool, prioritize those that offer two-factor authentication (2FA). 2FA adds an extra layer of security by requiring a second form of verification, such as a code sent to your mobile device, in addition to your password. This measure significantly reduces the risk of unauthorized access to your mining account. Enable 2FA immediately after registering with a mining pool to enhance the security of your account.
Another critical aspect of securing your mining activities is the use of strong, unique passwords. Avoid using easily guessable passwords or reusing passwords across multiple platforms. A strong password should be at least 12 characters long and include a combination of upper and lower case letters, numbers, and special characters. Consider using a password manager to generate and store complex passwords securely.
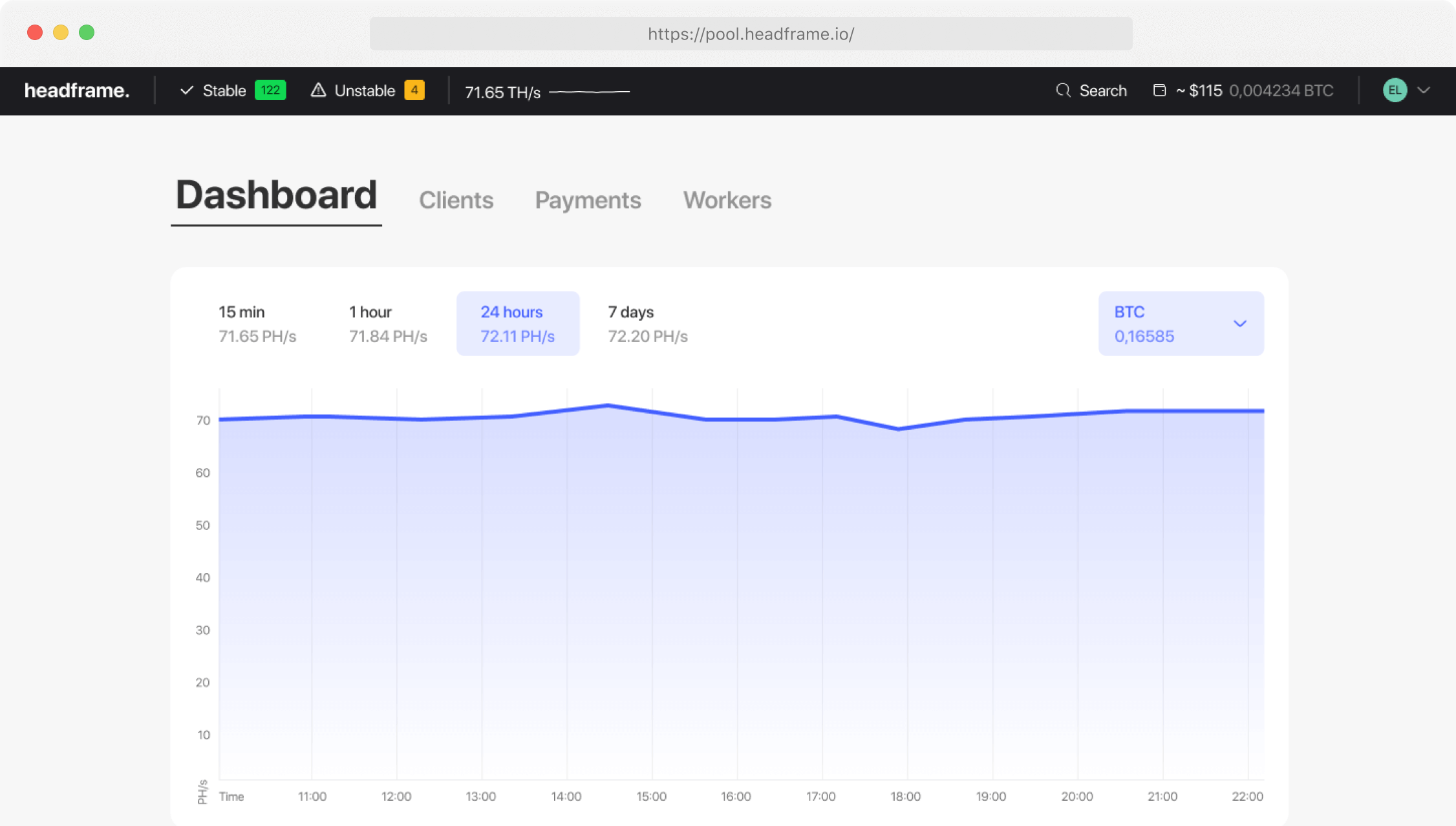
Regularly monitoring your mining account is essential for detecting any unusual activity that could indicate a security breach. Most mining pools provide dashboards that display real-time data on your mining performance and earnings. Familiarize yourself with these tools and check your account frequently for any discrepancies or unauthorized changes. Promptly report any suspicious activity to the mining pool’s support team and take immediate action to secure your account.
Phishing attacks are another common threat to cryptocurrency miners. Cybercriminals often use phishing emails and fake websites to trick miners into revealing their login credentials or downloading malicious software. Be cautious of emails and messages that request sensitive information or direct you to unfamiliar websites. Always verify the authenticity of any communication by checking the sender’s email address and looking for signs of phishing, such as spelling errors and urgent requests. When in doubt, contact the mining pool’s support team directly through their official website.
Securing your mining hardware is just as important as protecting your online accounts. Ensure that your mining rigs are located in a secure environment with controlled access. Physical security measures, such as locks and surveillance cameras, can help prevent unauthorized access to your equipment. Additionally, keep your mining software and hardware firmware up to date to protect against known vulnerabilities and exploits. Regular updates often include security patches that address newly discovered threats.
Network security is another critical consideration for miners. Mining operations typically require a stable internet connection, which can be a potential entry point for cyberattacks. Use a reputable firewall and antivirus software to protect your network from malicious traffic and malware. Configure your network settings to limit access to your mining rigs and disable any unnecessary services and ports. For added security, consider using a Virtual Private Network (VPN) to encrypt your internet traffic and protect your privacy.
Backup strategies are essential for safeguarding your mining data and wallet information. Regularly back up your wallet files and important account information to secure, offline storage devices. In the event of a hardware failure, hacking incident, or other unforeseen circumstances, having a recent backup ensures that you can quickly recover your funds and resume mining activities without significant losses. Store your backups in multiple locations to further enhance their security.
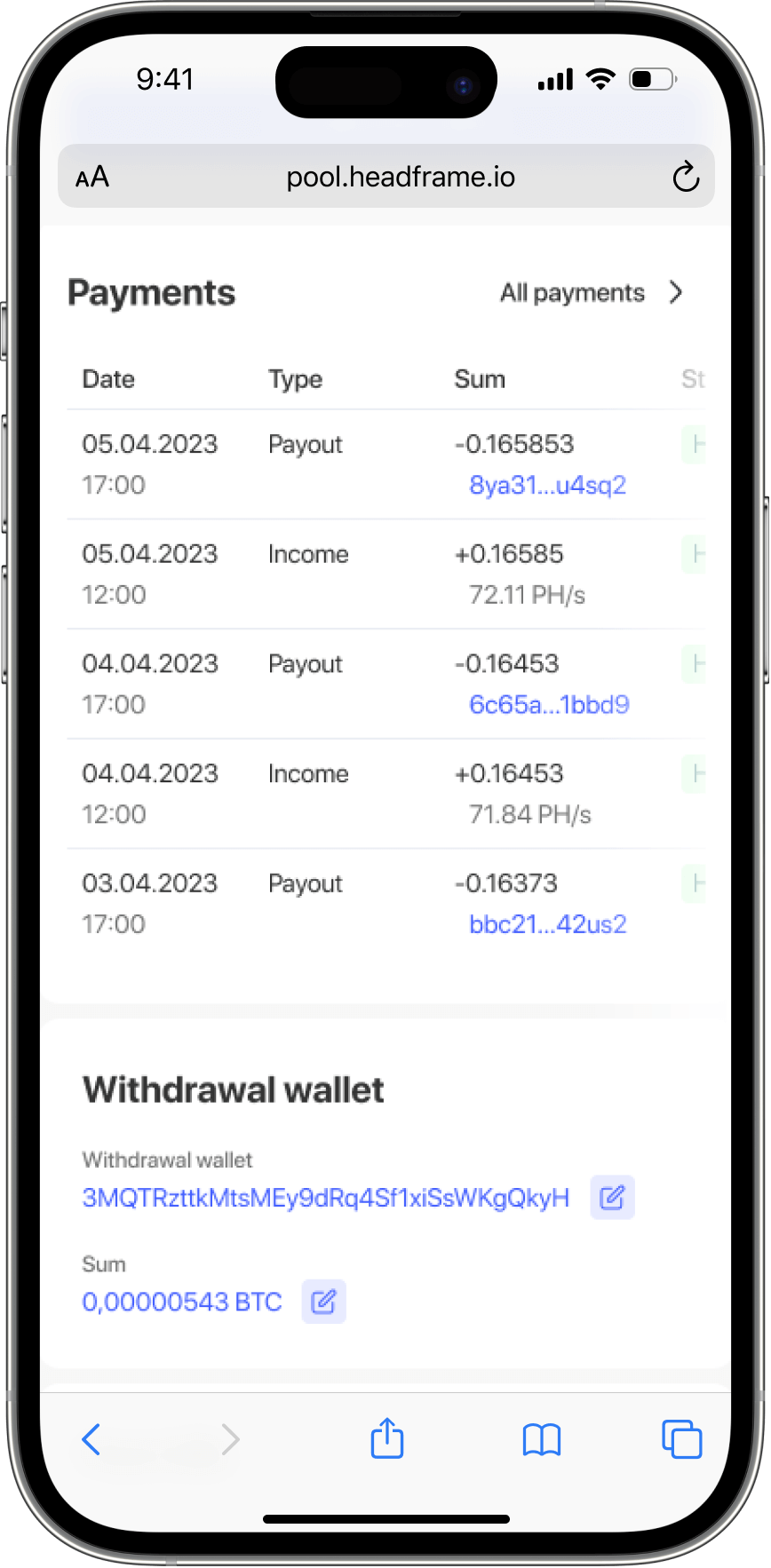
Mining pools often have specific payout policies, including minimum payout thresholds and scheduled payout intervals. Understanding these policies is crucial for securing your earnings. Choose a pool with reasonable payout terms that align with your mining capacity and financial goals. Be aware of any fees associated with withdrawals and factor them into your profitability calculations. Some pools offer automatic payouts, while others require manual withdrawal requests. Ensure that your payout address is correct and secure to avoid any loss of funds during the transfer process.
The decentralization of mining pools is an important aspect to consider for enhancing security and trust. Decentralized mining pools distribute the mining process across a network of nodes, reducing the risk of centralized control and single points of failure. This approach aligns with the core principles of blockchain technology and promotes a more secure and resilient mining environment. While decentralized pools may be less common than traditional pools, they offer additional security benefits worth exploring.
Engaging with the mining community is a valuable way to stay informed about the latest security threats and best practices. Participate in online forums, join social media groups, and attend industry events to connect with other miners and share knowledge. Community discussions often highlight emerging threats and provide practical solutions for mitigating risks. By staying engaged and informed, you can proactively address security challenges and protect your mining operations.
Finally, consider the environmental impact of your mining activities and implement measures to improve energy efficiency. High energy consumption not only increases operational costs but also raises concerns about the sustainability of mining. Optimize your hardware settings to reduce power usage and explore renewable energy sources to minimize your carbon footprint. Some mining pools are committed to promoting sustainable practices and offer incentives for miners who adopt eco-friendly solutions.
In conclusion, securing your cryptocurrency mining activities requires a comprehensive approach that addresses both online and offline threats. By choosing reputable mining pools with robust security measures, enabling two-factor authentication, using strong passwords, and regularly monitoring your accounts, you can protect your investments from cybercriminals. Additionally, safeguarding your mining hardware, securing your network, implementing backup strategies, and staying engaged with the mining community are essential steps for ensuring the safety and profitability of your mining efforts. By following these security tips, you can navigate the complexities of cryptocurrency mining with confidence and achieve success in this competitive industry.